Vulnerability Management
Identify, Assess & Mitigate Security Vulnerabilities Across Your IT Environment
Understanding Vulnerability Management
Protecting your organisation from security vulnerabilities is more critical than ever. CYB3R's Vulnerability Management services provide a comprehensive solution to identify, assess and remediate weaknesses across your entire IT infrastructure. By proactively managing vulnerabilities, we help safeguard your business against cyber threats, reduce risk and ensure compliance with industry standards.
Vulnerability management involves the continuous, systematic identification, assessment, reporting, management, and remediation of cyber security vulnerabilities across various endpoints, workloads, and systems. Security teams typically use vulnerability management tools to uncover vulnerabilities and implement processes for their remediation or patching.
An effective vulnerability management programme integrates threat intelligence and an understanding of IT and business operations to prioritise risks and address vulnerabilities promptly.
The Vulnerability Management Process
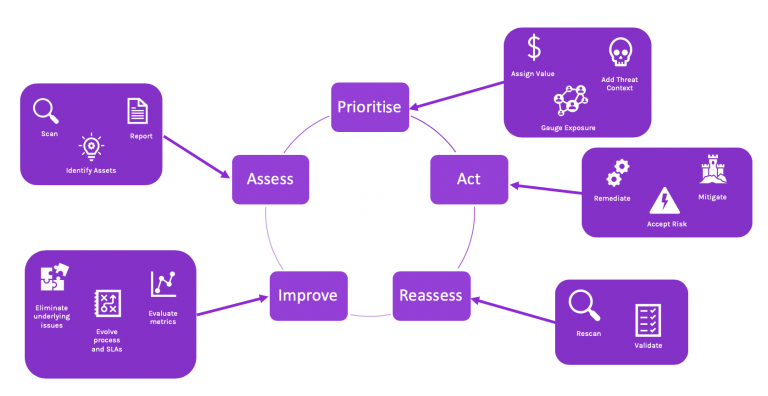
The vulnerability management process consists of multiple stages that should be followed within any vulnerability management programme. Although the specific terminology may differ, the core stages of the cycle generally remain consistent.
According to Gartner’s Vulnerability Management Guidance Framework, there are five preliminary steps that should be undertaken before the process officially starts:
This preparatory phase involves evaluating and measuring existing resources, processes, and tools to identify any gaps.
During this phase, security professionals should consider key questions to define the scope of the programme, such as:
Which assets will be assessed for vulnerabilities?
Which assets or hosts are critical to protect?
Who will be responsible for managing this programme, and what roles and responsibilities will they hold?
Upon detecting a vulnerability, what is the timeframe for remediation? What policies or service level agreements (SLAs) need to be established?
How frequently should asset assessments be conducted?What tools or software are necessary for effective host management or scanning?
Which specific assets or asset types will be included in the programme? In simpler terms, what is the context of the assets to be managed?
With this information, the implementation of the vulnerability management process can commence.
The 5 Steps of the Vulnerability Management Cycle
There are five main stages in the vulnerability
management cycle include:
Step 1. - Assess
Step 2. - Prioritise
Step 3. - Act
Step 4. - Reassess
Step 5. - Improve
Take the first step towards working with your new Vulnerability Management partner…
AI-Powered Vulnerability Management Strategy
AI plays a crucial role in enhancing security measures by automating vulnerability detection, threat analysis, and response for faster and more accurate protection against evolving cyber threats.
AI-driven vulnerability management significantly boosts efficiency, sharpens threat detection, proactively mitigates risks, and strengthens an organisation's overall security posture.
By harnessing machine learning algorithms, AI technology excels in identifying vulnerabilities, analysing patterns, detecting anomalies, and uncovering potential threats across network systems and applications.
Automation of Vulnerability Remediation
AI enables automation of vulnerability remediation processes by rapidly identifying, assessing, and responding to security vulnerabilities to reduce manual effort and response times.
Enhancing Security Posture
Integrating AI into vulnerability management enhances the overall security posture by providing real-time threat intelligence, predictive analysis, and automated response mechanisms for proactive defense against cyber attacks.
Automated Scanning
Smart vulnerability scanning tools automate the process of scanning IT infrastructure, applications, and devices to identify vulnerabilities, misconfigurations and potential security gaps.
Real-time Detection
Real-time vulnerability detection capabilities provide immediate alerts and notifications when new vulnerabilities are identified, enabling swift response and remediation actions to mitigate security risks
Continuous Monitoring
Continuous vulnerability monitoring ensures that security teams have real-time visibility into the evolving threat landscape, enabling proactive mitigation strategies and rapid response to emerging security issues.
AI-Driven Risk Assessment
Risk Prediction Models
AI-powered risk prediction models utilise historical data, machine learning algorithms, and threat intelligence to forecast potential security risks and prioritise vulnerabilities based on their impact and likelihood of exploitation.
Threat Intelligence Integration
Integration of threat intelligence feeds into AI-driven risk assessment processes enhances the accuracy of risk predictions, enables proactive threat mitigation, and facilitates informed decision-making for security teams.
Risk-Based Vulnerability Management
AI-driven risk-based vulnerability management prioritizes vulnerabilities based on their business impact, threat severity, and exploitability, allowing organisations to focus resources on addressing the most critical security risks first.
Common Challenges
Identifying Vulnerabilities
A significant challenge in vulnerability management lies in accurately pinpointing weaknesses across a multifaceted and ever-evolving IT environment, aiming to avert potential security breaches and data loss.
Risk Prioritisation
Efficiently ranking vulnerabilities by severity, potential for exploitation, and impact is vital for optimising resource allocation and addressing the most critical security threats swiftly.
Patch Management
Timely application of patches for identified vulnerabilities is essential to prevent exploitation by malicious actors and to maintain the security and stability of systems and applications.
FAQs
-
Vulnerability management is an ongoing process that involves regularly identifying, evaluating, reporting, and addressing cyber vulnerabilities across systems, endpoints, and workloads. Security teams typically employ specialised tools to detect these vulnerabilities and implement processes to patch or remediate them.
An effective vulnerability management programme prioritises risks using threat intelligence and a deep understanding of IT and business operations, ensuring vulnerabilities are addressed swiftly and efficiently.
-
According to the International Organisation for Standardisation (ISO 27002), a vulnerability refers to a weakness in an asset or a set of assets that can be exploited by one or more threats.
A threat is an entity or event that has the potential to exploit a vulnerability.
A risk arises when a threat successfully exploits a vulnerability, leading to potential damage or harm to the affected assets.
-
Vulnerabilities are typically assessed and categorised using the Common Vulnerability Scoring System (CVSS), a widely adopted industry standard that evaluates and communicates the severity of software vulnerabilities. Many cybersecurity organisations, including CrowdStrike, rely on CVSS to gauge the impact of vulnerabilities. The CVSS Base Score ranges from 0.0 to 10.0. In addition, the National Vulnerability Database (NVD) provides a corresponding severity rating based on these CVSS scores.
The National Vulnerability Database (NVD) also offers an up-to-date repository of Common Vulnerabilities and Exposures (CVEs), detailing rankings and essential information like vendor, product name, and version. These CVEs are curated by the MITRE Corporation, a not-for-profit organisation that started cataloguing them in 1999. MITRE provides fundamental details on each vulnerability, which are automatically synchronised with the NVD.
-
Vulnerability management is a continuous process, whereas a vulnerability assessment is a single, point-in-time evaluation of a host or network. While a vulnerability assessment is a crucial component within the broader vulnerability management framework, it represents just one step in the ongoing cycle of managing vulnerabilities.